Blogs & Articles: “A Doom Loop Of Lying” 🔗 8 weeks ago

- Category: Blogs & Articles | MyLegacyKit on Medium
- Author(s): MyLegacyKit
- Published: 2nd March 2024 21:29
Craig Wright once more perverting the course of justice with a clear cut case of fraud upon the court during the COPA v Wright trial
Written by Arthur van Pelt
ABOUT EDITS AND UPDATES to this article: as more material may become available after the publication of this article, it could have edits and updates every now and then. In that sense, this article can be considered a work in progress, to become a reference piece for years to come.
 Source: Twitter
Source: Twitter
“doom loop of lying” a quote from CryptoDevil — who picked up this phrase from the Bitcoin developers’ King’s Counsel Gunning exactly one week earlier — during live reporting on the final day of the COPA v Wright trial on March 1, 2024
Intro
Just when you think that things can’t get any worse anymore for Craig Wright during the COPA v Wright trial, he will surprise you (or not, for some) with the next grave digging move.
If I have to point to a spot where Craig Wright not only lost the COPA v Wright Identity Issue trial — and therefore the whole string of connected cases(*) — but also secured a forward to the UK Criminal Proscecution Services (CPS) for an advice if further criminal charges are appropriate… It’s on the moment described above by CryptoDevil. Justice Mellor will not take Craig’s answer there lightly, I think.
(*) Three cases have been halted by Justice Mellor, waiting for the outcome of the COPA v Wright Identity Issue trial: 2 passing off cases against crypto currency and digital assets exchanges Kraken and Coinbase, and the copyright/database rights/file format case against the Bitcoin developers and a series of companies active in the Bitcoin industry. Two other cases have been — voluntarily — halted too, as they also depend on the truthfulness of Craig Wright’s claim to be Satoshi Nakamoto: Craig’s appeal in the hodlonaut v Wright negative declaratory relief for libel case in Norway, and the UK libel case of Wright v hodlonaut. All these cases will almost immediately collapse in favor of the lawsuit opponents of Craig Wright when Craig Wright is ruled not to be Satoshi Nakamoto after the Joint Trial.
 Craig Wright is, contrary to what many in the BSV camp believe, claimant for the purpose of the Joint Trial
Craig Wright is, contrary to what many in the BSV camp believe, claimant for the purpose of the Joint Trial
This ruling has basically turned the original COPA v Wright case that started in April 2021 upside down. We now have to look at it during the Joint Trial as follows.
Craig: “I’m Satoshi Nakamoto, I own all Bitcoin copyright, I will prove it.”
COPA: “Go ahead. We will disprove all your (forged) evidence till nothing is left, your witnesses have no evidence either, so you are not Satoshi Nakamoto, you have no Bitcoin related copyright and you are a lying fraud on top.”
Mellor: “COPA wins on all three counts.” (We’re not there yet at the moment of writing, of course. But one can dream. It is in my opinion extremely likely that Craig Wright is not going to win anything in this case.)
Anyway. But this — Craig Wright being flipped to the position of the claimant instead of staying in the more relaxed position of the defendant as he initially intended when he provoked the COPA v Wright case in January 2021 — is the exact reason why we see him struggle with no less than four rounds of evidence that he has been trying to deposit in court. Because without exception, all these four rounds of new evidence have been called out by COPA as a mix of ‘not credible’ and ‘willingly and knowingly forged by Craig Wright’ documents and files.
A short history from one of COPA’s witness statements.

“4. It has become a familiar experience in this case to meet a major deadline such as the exchange of skeletons or evidence, only for Dr Wright to seek to add further reliance material an hour or two later such that it could not be addressed in a timely manner. So it is in this case. As the Court will be aware, this is now the fourth set of documents that Dr Wright has relied upon:
4.1. First, there were his original set of reliance documents, which were disclosed and nominated at the proper time. These were addressed in the first Madden Report and found to consist substantially of inauthentic documents (a finding with which Dr Wright’s own expert, Dr Placks, largely agreed).
4.2. Then, Dr Wright sought (and received) a second chance from the Court. He responded to the expert evidence by ‘discovering’ a new drive, from which he produced 97 New Documents as his second-chance Reliance Documents — for which permission was sought (and granted) at the PTR. Most of these were found to be inauthentic by way of the Fourth Madden Report and were agreed by Dr Wright’s own expert witness, Mr Lynch, to have been created in September 2023.
4.3. A little after ‘discovering’ those documents, Dr Wright discovered a third tranche of documents, his LaTeX files, and added a request for permission to rely on these at the PTR (though he would not disclose them beforehand). These third-chance reliance documents were said by Dr Wright and his solicitors to be of critical importance, yet were found to be entirely inauthentic by way of the Rosendahl report, and by agreement with Dr Wright’s own expert witness (Mr Lynch). These files were also said by Dr Wright to have no metadata: however, metadata did in fact exist and was available through Overleaf. Once that was (very belatedly) provided, it showed that Dr Wright had edited the LaTeX files in November and December 2023 (as is well summarised in MacFarlanes’ letter to the Court of 23 January 2024 and the raw data annexed to it: {AB-A/5/57}).
5. Following receipt of the various expert reports in relation to the 97 New Documents and the LaTeX Files, Dr Wright now seeks to rely on a yet further, extremely late, fourth tranche of 24 documents (the “the Application Documents”).” — Phil Nathan Sherrell’s 20th witness statement
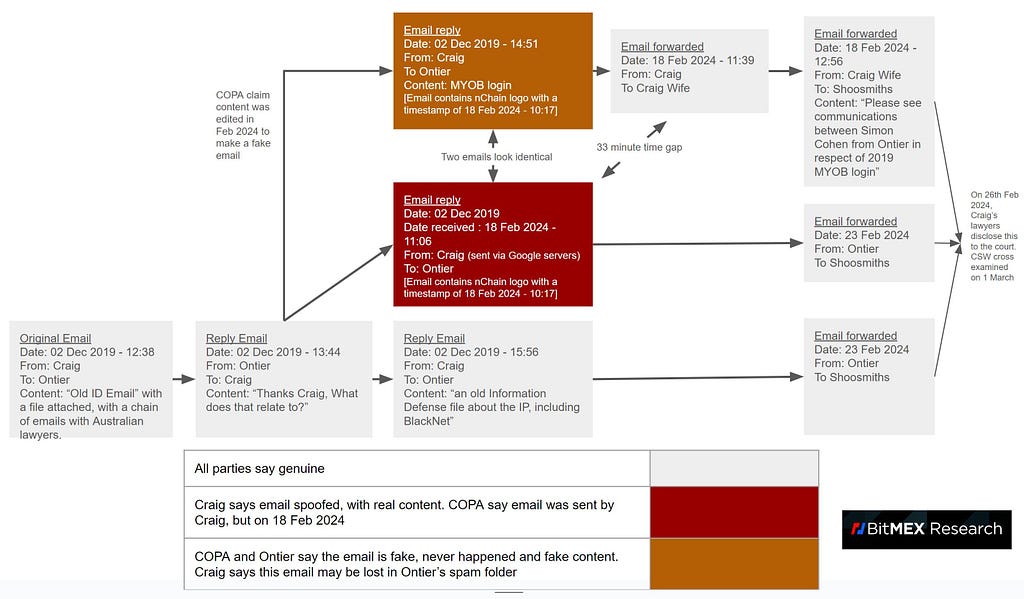
The Infograph by BitMEX Research
This email story I’m going to present today is pretty convoluted, if not quite complex to understand at first glance. However, just before publication, my friends at BitMEX Research created a helpful infograph with a summary of Craig Wright’s claims.
The reader needs to understand that COPA’s accusation is that what Craig calls a “spoofed email” is actually a “Craig made email forgery”. And as Twitter user ‘-ck’ said:
Even Mellor was flabbergasted enough to try to figure out what motive anyone would possibly have to execute such a ridiculously elaborate, perfectly coincidentally timed remote monitored attack with no logical motive.
BitMEX Research: COPA vs CSW — The ONTIER emails
“We have finally managed to express the Ontier email situation in a diagram that we believe is reasonably accurate. It shows that Craig claims:
- Someone spoofed an email from him
- This spoof email is identical to what he claims in a “real” email he sent
- The “spoof” email was received 33 minutes before the “real” email was sent”
The Final Trial Week: Monday February 26, 2024
So what exactly happened there on Friday March 1, 2024 that made CryptoDevil spit out “doom loop of lying”, the reader might ask?
For an answer to this question, we have to jump back to the beginning of the trial week. On Monday, February 26, 2024 (Day 16 of the COPA v Wright trial) Craig’s counsel Shoosmiths announced at the end of the day the finding of a Craig Wright related email thread that appeared to contain one or several “not credible” emails. It became rapidly known that Shoosmiths was forced by Craig Wright’s previous-previous counsel ONTIER to open up in front of the judge about this, for their client very embarrassing, discovery.
BitMEX Research, having a reporter on site during the whole trial, kept track of what happened that day in the court room in every fine detail, and they described their findings at the end of the day in “COPA vs CSW — Day 16 — Craig’s Lawyers Do COPA’s Job For Them”.
Their short but crucial blog article is kindly copied here in full.

“In court today, it was the turn of the COPA expert witness, Mr Patrick Madden. Cross examination occurred in the morning, and was over much faster than expected. COPA’s key witness was expected to testify over two days, but it was over in just one morning. The key point Craig’s barrister made was that it was possible to have a system configured, such that the signs of document manipulation could be put there by the software. Mr Madden often explained that yes this was technically possible, just not likely or feasible. Anyway, this cross-examination was over pretty quickly and then as we entered the afternoon, the court was then hit with some damaging surprise revelations from Mr Wright’s own legal teams.
MYOB screenshots
These revelations relate to Craig’s MYOB accounting records, which have come up a lot in this trial (Three times to be precise, day 4, day 15 and now day 16). Screenshots of the output from this accounting system have been provided by Craig as evidence in this trial. The output shows the transfer of Bitcoin from one of Wright’s companies to another company (Information Defense to Wright International Investments), for £795,000. The transaction is dated August 2009. If this document was authentic, it would support the claim that Craig Wright is Satoshi Nakamoto. Screenshots from the MYOB system are shown below.
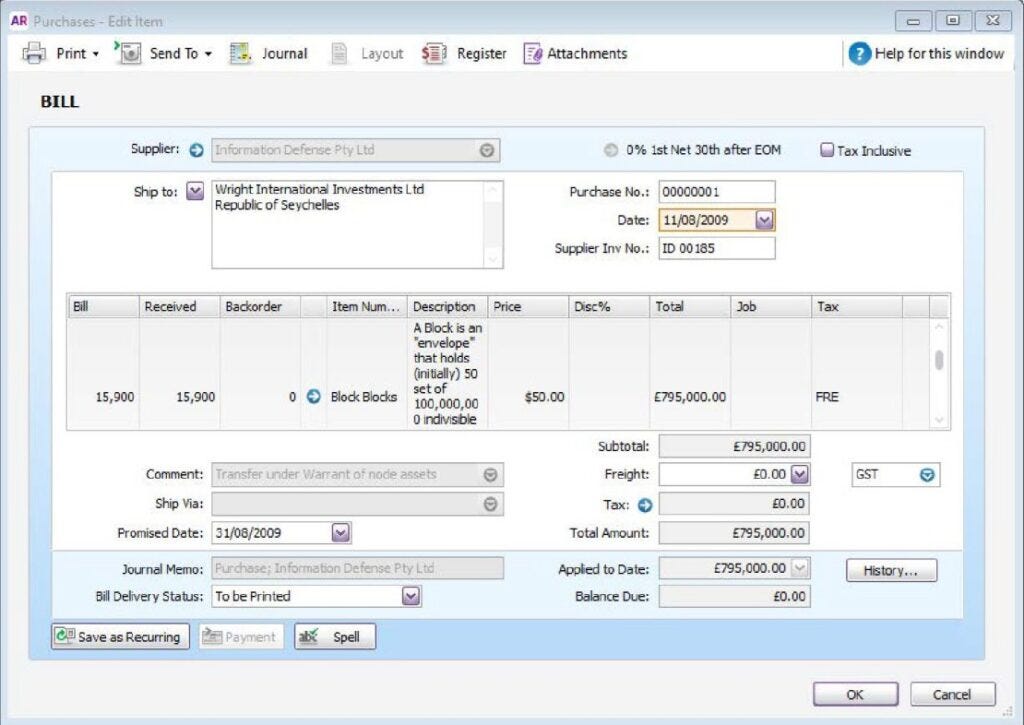
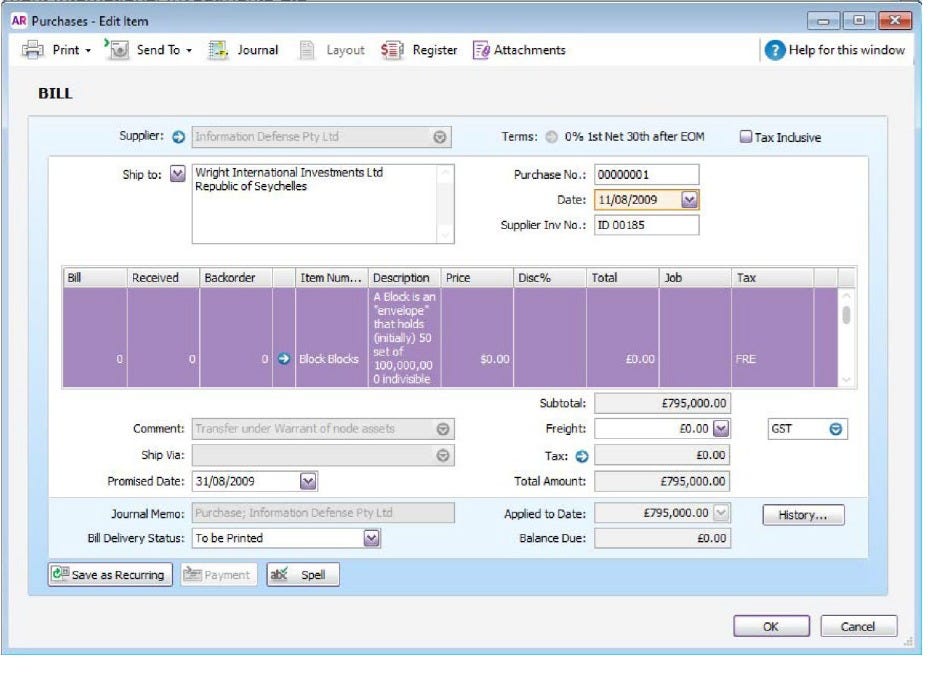
However, COPA alleges that the screenshots were not made until 9 March 2020. The evidence for this is from the COPA expert witness, Mr Patrick Madden, who obtained the raw log files for the accounting software which date the entries to March 2020 and the screenshots must have taken place after the accounting entries were made. In response to this, Craig told the court that the records could not have been made in 2020, since the screenshots were provided by his old lawyers, Ontier, who produced the documents in 2019.
Disclosure from Craig’s lawyers
In court on 26th February 2024, Craig Wright’s own barrister, Lord Grabiner, was compelled to show a letter to the court, a letter from Craig’s old lawyers (Ontier), to his new lawyers (Shoosmiths). This was evidence in court, which was especially damning to Mr Wright. Given how this case has progressed, this is not particularly unusual. However, what was unusual is that was being presented by Wright’s own barrister. It was almost as if Lord Grabiner was doing the work of the COPA barrister Mr Hough. As a result, Mr Hough almost had nothing to say.
A summary of the content of the letter is provided below
Date: 8 February 2024
From: Ontier
To: Shoosmiths
1. Dr Wright first provided this firm with login details for the MYOB accounting software on 9 March 2020 and we first accessed the software on that same date. We did not have access to MYOB in late 2019.
2. We created a series of screenshots from that system on 9 and 10 March 2020.
3. We are not aware of AlixPartners having access to MYOB in late 2019. They can confirm the position.
Lord Grabiner then went on to disclose an email from Mr Wright’s wife, Ramona Watts.
A summary of an email from Ramona Watts (Craig’s wife)
Date: 18 February 2024
From: Ramona Watts
To: Shoosmiths
Please see communications between Simon Cohen from Ontier. In respect of 2019 MYOB login, Ontier has said that they only received login details in 2020, but they, as well as AlixPartners, had it in 2019 as Craig has explained.
The above email forwarded another email, which contained the MYOB login details being sent to AlixPartners and Ontier, it was dated on 02 Dec 2019. This email was part of a chain. Firstly Craig emails the login details to Ontier. In the second email, Simon Cohen of Ontier replies and say’s ”Thanks Craig.”
Doing COPA’s job for them, Lord Grabiner then pointed the court to Mr Wright’s testimony in this trial.
23 February 2024 — This trial
Question from COPA: You told the court that Ontier received MYOB login details in late 2019, didn’t you?
Craig: “I did, and I have the emails for it”
Lord Grabiner then disclosed a second damning email from Mr Wright’s old lawyers.
A summary of the second email from Ontier to Shoosmiths
Date: 23 February 2024
From: Ontier
To: Shoosmiths
We have searched our systems. We can confirm that we have located the attached email which on its face is dated 2 December 2019 and contains the same text as the email attached to your email timed 11:51. However, our attached email was in fact received on our systems on Sunday, 18 February 2024. This is confirmed by the email metadata, which can be reviewed by viewing the properties of our attached email. For the avoidance of doubt we have compared the email properties of the email on our systems to those of the email attached to your 11:51 email and they substantially differ.
In light of the above, we are of the view that the email attached to your 11:51 email is not genuine. Understandably, we are keen to ensure that the court is not misled. Please provide us with a copy of the transcript of today’s proceedings and confirm by return how you intend to proceed.
Lord Grabiner then showed the court the two versions of the emails. In a bizarre moment, it was Lord Grabiner doing COPA’s job of proving to the court that Craig (or his wife) had faked documents. Indeed, Grabiner had to do this, as the email above said, Craig’s old lawyers demanded that this was raised in court and asked for the evidence. Grabiner said as follows:
So, my Lord, if your Lordship holds side by side the, what I call the Ramona version next to the Ontier version. So we can just have a look at that. It’s from Craig Wright, 2 December 2019, and again, this is a three email chain, but the top email, of course, is an entirely different content.… But if you compare the two, your Lordship can see that the top email is entirely different and both purport to be in respect of the 2019 communication.
The original 2019 email contained content with some information about the BlackNet system. In this remarkable turn of events, Grabiner was proving to the court the nefarious shenanigans of Mr Wright.
The rest of the trial
At the start of today’s proceedings, Craig Wright’s barrister asked for a report from a new expert witness of his to be submitted as evidence. This expert is called Mr Peter Bryant. This is presumably because Craig thinks his current expert, Dr Placks is “unqualified” and “unskilled”. However, amazingly, on the same day, a few hours later in the afternoon, this request is withdrawn. As Mr Wright’s barrister put it:
Dr Wright is not pursuing an application in respect of Mr Bryant
Mr Wright also indicated that he no longer wishes to examine various other witnesses, including his own expert Dr Placks. This means COPA will not be able to cross-examine Dr Placks either and therefore the judge is likely to treat COPA favourarbly with respect to this evidence. This just leaves a few more witnesses left. Mr Rosendahl tomorrow is due to be examined tomorrow. After this and a couple more witnesses, we will having closing arguments and then the trial will finally be over. Things are getting faster now, just a few more days left.”
COPA’s barrister, Hough KC, was quick to reply that they would not comment yet on the new situation, given that COPA’s forensic expert Madden still had to forensically inquire the emails. His report about the emails was to be expected on Wednesday. An impetus was already given to reserve the following Friday for follow-up cross examinations of Craig Wright and Patrick Madden.
And also CoinDesk was on it.
“Emails shared by Craig Wright’s wife as evidence in the ongoing trial probing whether he’d invented bitcoin (BTC) are “not genuine,” Wright’s former lawyers said in court, as the fourth week of the legal proceedings kicked off Monday in London.
The emails between Wright and his former representatives at Ontier became part of the trial after the self-proclaimed bitcoin inventor referenced them while he was under cross-examination last week. The emails were then shared by Wright’s wife Ramona Watts with his current counsel at London law firm Shoosmiths, who in turn reached out to Ontier to confirm their accuracy.
Wright claimed Ontier had access to the Australian accounting platform MYOB in 2019, and that he had the emails to prove it. Those emails that Wright’s wife then shared with Shoosmiths were doctored, according to Ontier.” — CoinDesk
The Final Trial Week: Wednesday February 28, 2024
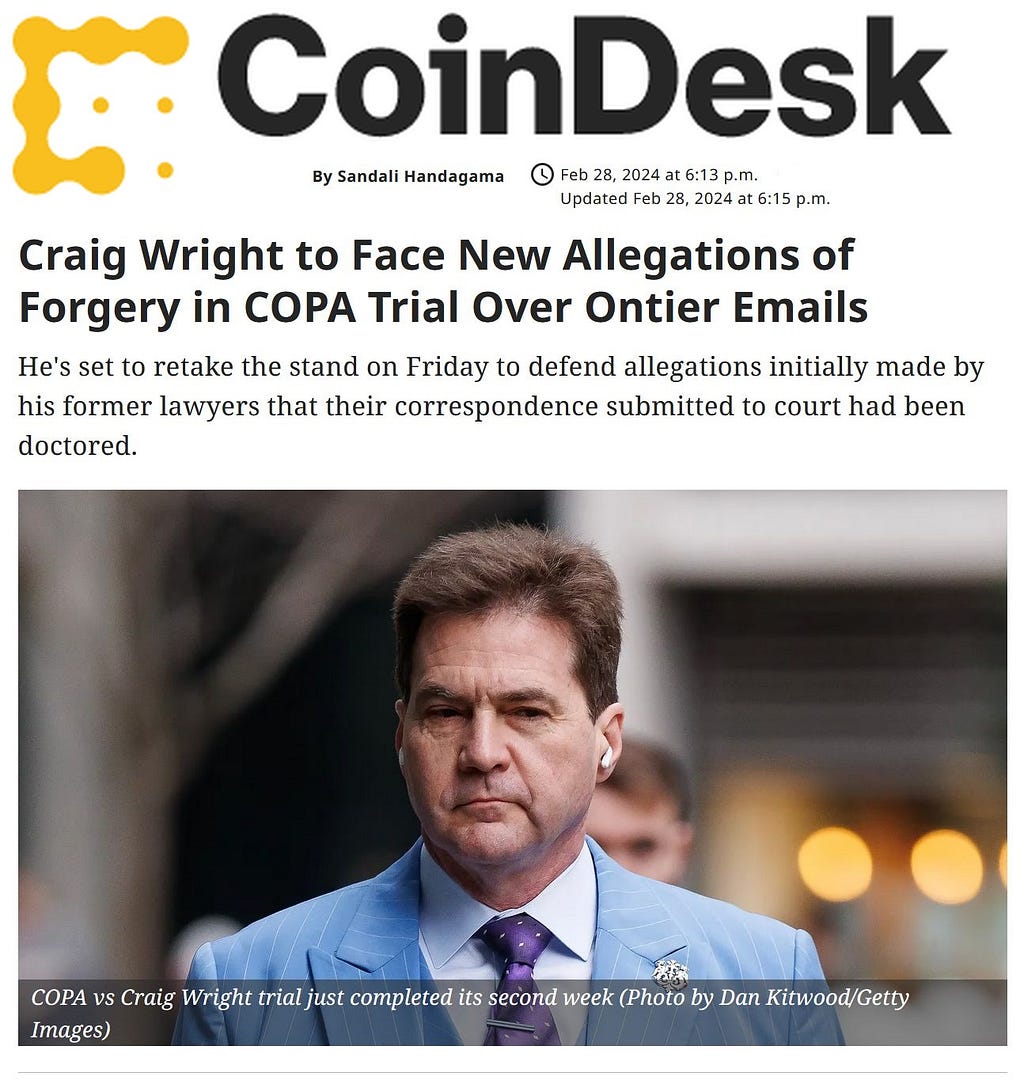
“All witnesses in a U.K. trial challenging Australian computer scientist Craig Wright’s claims of inventing popular cryptocurrency bitcoin (BTC) are through testifying — save for a potential return appearance by Wright to defend emails his former lawyers have alleged were faked.
Although Wright went through cross-examination for several days during the weeks-long trial, which began on Feb. 5, he’ll likely take the stand again on Friday morning to defend the new allegations, along with digital forensics expert Patrick Madden from the plaintiff’s side.
After Wright made a reference last week to some emails between him and his former legal representatives at Ontier, his current lawyers were compelled to submit those emails to evidence. An inconsistency forced them to check with Ontier on the accuracy of the correspondence submitted by Wright’s wife Ramona Watts. Ontier then responded the emails appeared to be “not genuine.”
COPA is set to put the new allegations of forgery to Wright on Friday.” — CoinDesk
Reality was indeed, Hough KC announced the Madden report on behalf of COPA, his sixth forensic report already during this lawsuit, and the Friday cross examinations that will be starting at 11:30 local time due to Justice Mellor having another hearing in the early morning, are set.
The Final Trial Week: Friday March 1, 2024
And so the Friday arrived. For a minute to minute report of what happened on this day I turn to ‘CryptoDevil’ and ‘Robin Nakamoto’ who both did, as always, an awesome job of catching the moods and the words of the participants in the court room.
Since it was a short day in court with only two people on the stand, the transcripts are rather easy, but still worthwhile, reads. They give a beautiful insight in the brain of a con man who just cannot back out anymore, and who just has to pile lies on top of previously outed lies that got debunked.
It’s a doom loop of lying indeed.
Craig Wright on the stand, by CryptoDevil

This extraordinary additional appearance of Craig Wright is about to commence!
It comes courtesy of clumsily forged emails his OWN counsel had to disclose to the court only SEVEN minutes after they’d just blamed other forgeries as surely being the work of nefarious hackers!
For a while it felt like the stream was not going to be happening as it over-ran the expected 11:30 start time for an agonising SEVEN minutes, before we were all treated to a short audio-only stream of the court busily taking their positions!
Curtain is up!
Grabiner starts saying that @dr_cswright needs to be re-sworn and confirm his new witness statement.
The Hough talks about their position being subject to 3 matters and that they should be allowed to put CSW’s explanations to expert witness Madden.
H: That secondly, Mr Madden’s cross should be the last word, no more statements from Wright and that the Tulip Trading dot net domain was registered from 2008 to 2014 but by somebody wholly unrelated to CSW or anything to do with him.
H: Now handing out some docs to the other side. “Lordship will have seen that CSW places some reliance on RCJBR and Tulip Trading dot net domains being set up with particular settings. Some research has been done and what we say it shows that the SPF validation has been set up last week. That the preceding SEVEN years it had been blank. The TXT record also shows no entry (prior to a few days ago) and now shows one as of TODAY. The security trails page has not yet picked up these new configurations as you see the supertools platform has picked up these new changes to the domains”
Grabiner interrupts.
G: “It is more appropriate to leave this to the witnesses”
H: “If we had been able to include it for witness statements (due to it being done so recently) we would have included it”
Mellor mingles in the discussion.
M: “Yes reading CSW’s statement it does beg the question as to when these DNS entries were modified”
G: “Yes we do not object to Mr Hough’s presented facts. There is an issue in para 6 we feel should be raised”
M: “I have a recollection this point has already been challenged”
M: Asks for CSW to be sworn again
CSW: swears himself in
Grabiner: Asks him to confirm his 15th Witness Statement.
 Jonathan Hough KC
Jonathan Hough KC
H: “CSW you have been called in for one purpose, the documents you submitted earlier this week. The background of the issue is, when you first gave evidence you stated that your former solicitors had gained access to your MYOB account in 2019”
W: “Correct”
H: “That they had subsequently disputed this and said that it was only in 2020. And that that Ontier’s version was put to you on the 8th February and you claimed that you had access to emails from 2019 which showed they had access to MYOB in 2019. That you had provided login details then”
C: “Yes”
H: “Going back in time to 2019, on screen a chain of 3 emails December 2019 at the bottom an email from you to Simon Cohen of ONTIER saying ‘see attached’ which showed a chain of emails from your previous counsel in Australia concerned with your Australian companies. And that Mr Cohen replied saying ‘thanks Craig what does this relate to’. And that you replied to that question accordingly describing it as an ‘old Info Def IP’ email discussion. That this took place on 22nd December 2019 and this is a genuine exchange of emails”
W: “No, it is a partial exchange of emails. It does not contain the follow up from Alix Partners talking about MYOB”
H: “You are aware Mr Cohen is no longer at Ontier LLP”
W: “I am”
H: “The email at 11:39 from your wife Ramona saying ‘Simon’ and then no text. And at the top 12:56 forwarded to your current counsel and the text ‘please see comms from Mr Cohen 2019 re the MYOB access they had then. Do you see that?”
W: “I do”
H: “It is correct that the one at the top was a genuine email from your wife to Ontier”
W: “Yes, I didn’t send it though”
H: “And the one at the bottom was a genuine one from Ontier”
W: “Yes”
H: “That you had then forwarded an email on to your wife and that it would be transmitted on to Shoosmiths“
W: “No but my wife chose to send it on”
H: “You didn’t know?”
W: “She told me I didn’t object”
H: “On the screen [comparing emails side by side] what we see is the 2 emails we are discussing. The one one the left showing what your wife sent recently and the one on the right showing what you had sent to Ontier in 2019”
W: “Yes I do that, I respond to emails twice”
 Craig Wright meme. Source: Twitter
Craig Wright meme. Source: Twitter
H: “The chain you had sent to Shoosmiths was NOT the one you had sent to Ontier in 2019”
W: “No it was part of a migration from my RCJBR mailbox as I had been receiving threats from many people”
H: “Going to Mr Madden’s report, he records the Ramona version along with others contained a logo image for nChain and that image contained a property. That timestamp is only explained by this email being created in this form in December 2020”
W: “No it is when that email was downloaded. Mr Madden has not done an experiment. What he has done, My Lord, you set up a GMAIL”
H: “We are not talking about that”
W: “WE ARE. WE ARE TALKING ABOUT setting up an email account server and then he has [goes into long rambling technical irrelevance]”
H: “CSW you are making an entirely different point. This email would NOT contain an image from 18th Feb 2024 if it had been written 5 years previously”
W: “No, that’s not true, I don’t use Outlook, I use Google and that saves as an eml format and that means when you download it changes it” *hitting the water like a drunk on vodka now*
H: “The initial time of sending is shown as timestamped on the google server”
W: “No actually the original email won’t have a receive from Google”
H: “No, I put it to you that is not correct. It shows a send time of December 2019 which is in stark contrast to the image timestamp of 2024.”
W: *waffle commences about emails between internal Google machines*
H: “Under para 27 the est mpsa received timestamp in the transmission head for the Ramona version to Shoosmith of 22nd December 2019 is 21 characters in length. Gmail changed it’s format in 2022 to 71 characters in length, so the timestamp is not consistent for the time period”
W: No [more techical waffle about the google takeout having different parts]
H: “We disagree about that. This email exchange between Shoosmiths and Ontier the timing of this email is within an hour of when I had put it to you about your claim of 2019 and you had said you had emails proving it. That email attached the Ramona document dated on its face to 2019”
W: “No it is not a valid email, it has been spoofed. I had DMARC which is a secure authorisation since 2016. Google DCMARC is the full encrypted system but SPF will generally go into a spam box and be rejected”
H: “Sorry which are you saying is a spoofed email?”
W: “The one which was sent to Ontier”
H: “No we are talking about the email chain they sent to Shoosmith that contradicted the one your wife sent. You don’t say that was a spoofed email”
W: “Well unless I could see the header. From the headers *blah blah blah about manually setting dates*
H: “Do you say the one that referred to MYOB login was spoofed or the Info Def one?”
W: “Well that depends you cannot tell unless you look at the header. There was an email which was spoofed that was sent to Ontier and on the header you can tell if it was spoofed”
H: “We are looking at an email you sent to your wife and she sent to Shoosmiths on the 18th February. Which one is spoofed?”
W: “The one which came from Google”
H: “I put it to you the one on the right is a fake backdated one and you say it is NOT spoofed. The one on the left where Shoosmiths asks Ontier to check their mail servers to confirm the email contents they responded saying they had located the 2019 email and they attached it which showed the same text of the Ramona email but that it was sent to them on 24th Feb 2024 and that it contained emails in it which were different from the original 2019 chain. That no link to the MYOB login was sent in the original 2019 chain”
W: “That’s what they say, I’ve seen different”
H: “We are talking about these emails chains”
W: “What they’ve done is one of those emails is a spoofed email [vague waffling about headers]”
H: “This email provided to Ontier by Shoosmith February 2024 which is identical to Ramona’s except where Ontier’s system has ‘shared’ in it but other than that those two are identical”
W: “No there are also diffs in mime type et cetera. If you print out from Outlook I can make it look the same but it would be different”
H: “With exception of the word ‘shared’ and ‘ext’ what do you say are the differences”
W: “Well the on the face, we can see that those who spoof emails would [blah blah]”
H: “Let’s just look at the contents what are the differences?”
W: “You can’t tell by looking at them, that’s why people spoof emails, that’s why Adam Back did…”
H: “No what are the differences in the text between these 2 emails”
W: *off topics waffle*
H: “My Lord please instruct the witness to answer the question”
M: “I’m not sure it is necessary to do”
 Lawyer Gross explains ‘res ipsa loquitur’ (it speaks for itself) to amateur armchair observer in the BSV camp. Source: Twitter
Lawyer Gross explains ‘res ipsa loquitur’ (it speaks for itself) to amateur armchair observer in the BSV camp. Source: Twitter
H: “Indeed. Moving on this version we can see Ontier pass on the one they received from 2024 and the transmission header highlighted in green the timestamps for the creation of the email which would be set by the system time”
W: “No, you see My Lord that goes back to the 1980’s and you could use a command line to manually set [talks about date and frog] RSC822 etc”
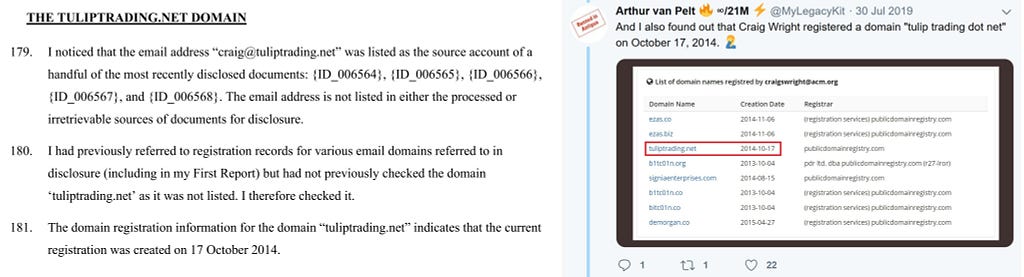
H: “No, I put it to you that the timestamp in this instance is set by the local computer clock”
W: “No it can be set any way you want”
H: “The timestamps for the transmission severs show the same time”
W: “No, you see this has policy issues with mimecast and what this shows is someone with a mimecast account and they’ve connected to mimecast and filled out the information”
H: “No, what we see is the timestamp”
W: “No, what we see is spoofing *waffles*”
H: “No, what we see is the series of timestamps on the mailservers”
W: “No, what we see there are errors in the Google information”
H: “CSW you have suggested over the last 10 minutes that this email was a real email which was spoofed. Who do you say did this and why?”
W: “Who is easy I have mentioned it in court before and *goes off into long and rambling discourse on spoofing* Email is the most incredibly easy thing to spoof, that is why I have DKIM and SPF and ARK signed message as you can see on my domain”
H: “CSW what you are saying is someone would need to get a copy of your email and set up a spoofed version to send to your solicitors”
W: “No, I could type date: frog and the email server would accept it. Yes someone has a copy of my email *talks of dozens of people who have copies of his emails*
H: “So someone has managed to get an original copy of your email and they have spoofed it to send to Ontier?”
W: “My email is so shared now it’s not funny, I noticed on the weekend people like Arthur van Pelt sending files that should not have been public, from COPA.”
 You called, Craig?
You called, Craig?
Seriously though, Craig Wright was most likely referring to continuous ‘leaks’ that I provided, leaks like the one below that I tweeted from the official COPA DropBox that Craig apparently had no idea of that it even existed.
“COPA’s forensic expert Madden released his 5th report 1.5 weeks ago (February 18, 2024) and he debunked several forgeries of Craig Wright based on an email address he found.
Guess who figured that out in 2019 already.”
And now, quickly back to the fourth week of the COPA v Wright trial again.
H: “CSW no what would be required is that somebody would have to get a whole of your original email and modify it to spoof it and send it on”
W: “NO! This is one of the simplest things you could do this is script-kiddy level of difficulty, the Tulip Trading case I had a hack where all of my files were taken. Employees had hacked and taken files and emails, my wife’s, Alan Granger, Stefan Mathews other people…”
H: “CSW the digression can end. Your latest witness statement where you discuss the SPF that allows soft fails and you set up TulipTrading dot net and RCJBR for Google servers, do you see that”
W: “I do”
H: “You go on to make a reference to Mr Maddens reference to a soft-fail and say that it doesn’t align with the record. You said this to take issue with the content in the transmission header [which was shown on the screen meanwhile]”
W: “Yes I was…”
H: “You were taking issue with the header information in the Ontier 2019 and email you have said was genuine. The transmission header there [reads info] see that?”
W: “I do”
H: “That Madden refers to SPF and soft fail. You were making points to attack it but you said today it was genuine”
W: “No, it was an irregularity, Google would have sent it to the spam box, they would have had to go there to retreive it, that’s what happens with mimecast”
H: “CSW all your evidence is set to attack THIS email Mr Madden highlights, but you said today that it was a genuine email”
W: “NO. What I said was [goes off into odd rant about spam folders and irregularities]”
H: “CSW your 15th Statement gives reasons to say how this email might have been spoofed and now you say how it was a genuine email”
W: “No *waffle*”
H: “You are contradicting your own witness statement”
W: “No because if mimecast would have put them in the spam folder, My Lord, and after 30 days it would have been deleted and if I had sent one and said I have sent one to you, Simon Cohen, it’s possible he had received 2 and one may have ended up in the spam folder”
H: “No your witness statement does not say that”
W: “No, because I intended to come here and say it”
H: “My Lord, may I hand these out. CSW if you look at the 1st of these security trails reports showing the txt value for the rcjbr domain was first seen by this tool on 28th Feb 2024”
W: “NO this was only partial information this domain was set up as a DMARC domain which means DKIM signatures which have to be set up with the SPF for ARC and what you have here is 1% of what you need for that and when you pull down the information for google which shows it all from 2016 and google require all this to be included and when you run a domain it is run by google and you are not picking up the information which is recorded by Google”
H: “No CSW what this shows is that you added this information on the 24th February”
W: NO YOU SEE, MY LORD, what this shows is *unbounded waffle*
H: “No, this shows it was added in the last week doesn’t it?”
W: “No, this is Google, *faces judge* what this does is show that Google handles the domain and what you set up is done by Google”
H: “No, CSW what this shows is the SPF information for this domain had not been set up by the date as shown in your witness statement”
W: “No, you see that’s Google and how they set up property records and when you do rjcbr dot org the whois records turn out differently and I’m not sure *picks paper up to show* why you have this url data which is how people are deceived and what yours shows are dots”
H: “You are saying this site has been spoofed?”
W: “You see this domain has been going back to 2011 and what you will see is *generously slathered waffles*”
 Source: Twitter
Source: Twitter
H: “No, what we can see is the information had not been entered at the time the site info had been crawled”
W: “No, what this shows is that Google handles this and it is an advanced security version and that shows here going back to 2017 at least that it has been added”
H: “I put it to you that you added this information on the 24th of February to back up the story you are now given”
W: “No you see it is the weakest form of security”
H: “CSW you previously said it was what you relied on”
W: “No you see it is Google and [goes off on one]”
H: “No CSW you see this 2019 email simply shows that it had nothing to do with MYOB”
W: “No becaus I spoke with [Alix Partners person] who’d said they had the MYOB login details in 2019”
H: “No that’s simply not true. You had claimed Ontier had login details to MYOB before 2019 and the only evidence you have is this fake email”
W: “No, it is not a fake email and lawyers don’t want to show all their emails”
H: “So you are saying they are withholding more emails?”
W: “No you see Alix Partners *waffles insistently*
H: “No we are talking about this email, are you saying there is another one out there?
W: “Being that Alix Partners got their login details in 2019 and because Alix Partners were engaged by Ontier then that is how they got the access to MYOB in 2019”
H: “There is no evidence which supports that claims, what you did was backdate your computer clock in order to send this email didn’t you?”
W: “No, because you can set it manually you can put date:frog and I am going to keep saying that because you can put anything you want. What matters is the Google server and what it has is 2019 and what I have in my spam folder is a received message where someone had attempted to spoof this message and it is me and Ontier who received this email as though it was from me”
H: “CSW this is very straightforward you had sent the backdated email to Mr Cohen at Ontier where it was received”
W: “No actually! What was sent was manipulated by mimecast”
H: “No, you sent it to your wife who then forwarded it on to Shoosmiths”
W: “No, you see, My Lord, what you get is Google takeout will record the date of the email when it was sent and Google will not trust the date you send and it will put its own server time on it without exception”
H: “CSW you FORGED an email during trial to back up your claims, didn’t you?”
W: “No, you see, My Lord, what you do is you send and email and Google will check and imaps will only work within one hour and if your clock is out by more than one hour Google will not send and that’s why Madden did the change he did and then put it back”
H: “CSW your counsel can put questions to the expert witness but what I put to you is that you sent this forged email didn’t you?”
W: “No, you see, My Lord, *addressing the judge repeatedly now* someone sent an email to me AND to Ontier”
H: “CSW I am giving you ONE LAST CHANCE to confess to this forgery as it may be important to relief. You forged this email didn’t you?”
W: “No you see what happens is on outlook it does [doom loop of lying & irrelevance about state level attacks needed]”
H: “Those are all my questions”
Gunning KC of the Bitcoin developers takes over from Hough KC.
G: “Can I just bring up that you took objection to a URL meta character in the web address. It looks a bit like a dot”
W: “Yes, it’s not a full stop”
G: “This is your statement and you show the Tulip Trading website url and that also has the same blobby dot”
W: “You see I brought it up as it doesn’t have it for 2015”
G: All my questions”
Orr KC, Craig’s own barrister takes over now.
O: “Can I just ask about the question put to you ‘that was starkly in contrast with the image timesamp’ and you said ‘that’s only partial as the email is split in to two parts’ can you explain what you meant?”
W: Because I was getting so much hate in 2019 I changed my domains and removed RCJBR dot org for a year. Because I had done that and the migrated across Google, the way they have it in takeout it has the first part of the header as craig @ rcjbr dot org and I have no idea what Google logs me as”
O: “Please explain what this doc is
W: “Without the header I have to assume that it is craigwright at rcjbr dot org and if so it is the first half of the email which was extracted”
O: “You also raised the importance of the SPF record”
W: “I do”
O: “You see in Mr Madden’s report the header showing 18th Feb 2024 do you see any reference to SPF checks in that header?”
W: “Unless you can point them out I can’t see any”
O: “If there is no reference to SPF checks what is the significance of that”
W: “That’s a really big problem because google does all these checks and the only way you can have that is if this email is old, which this one isn’t and you have a mimecast et cetera and you can send and spoof bulk emails, which is what mimecast does allows you to broadcast without doing SPF checks”
O: “Those are all my questions”
Justice Mellor still has a few things to say.
M: “There’s one thing you can help me with. You see where you were asked ‘who did this and why’ you are being asked about the email you say was spoofed. The issue of who and why are not separate, you say why but not who. You mentioned there were over a hundred people, can we not be more specific?”
W: “No, I have been involved in many companies and some people have fled the country. And certain Reddits have had this information and Mr Arthur van Pelt has been showing screenshots and they want me to fail and are acting against me”
 Yes, Craig? You called again?
Yes, Craig? You called again?
M: “But if they are acting against you why send through an email which purports to support your claim?”
W: “No you see it is easy to spoof an email and without SPF checks it would end up in your spam box and if you went through your spam
W: “you would find it and why would I only have done it a few weeks ago was because it was sent to Ontier and one was sent to me and in my google takeout there is one which contains the message but I’m not running Outlook”
H: “So your position is the person who you say did this just happened to send it as the timestamp shows at the same time your wife sent through the real version of the same email and that was a complete coincidence?”
W: “I don’t know, I haven’t had my house swept for bugs yet. Diligence have come through my house twice, they swept for bugs and I have been broken into twice and they found cameras and bugs”
H: “All my questions”
M: “Hopefully this will be your last appearance Dr Wright”
H: “Hopefully yes”
Break until Madden at 14:10
 Craig Wright’s lies always work well with his fan club
Craig Wright’s lies always work well with his fan club
Craig Wright on the stand, by Robin Nakamoto
COPA v. Wright — Day 69420 🤷🏻♂️ 🧵
GM — I didn’t manage to go to bed before 5am 😳 nevertheless I’m on my way to the Rolls Building.
I’m pretty positive (but not 100% sure) that today the Hough and Gunning will cross examine Failetoshi and discuss the Madden report on the latest forgeries. Today is the last day before the oral closing (in a week time). Either way it’s gonna be a great day *except for Craig Wright.
I made a drawing to sum up what we can expect today in court .
Are you ready?

Robin Nakamoto on Twitter: "Sorry, I struggle with priorities (my ADHD 🙌🏻), but while I was sipping my coffee, I realized that today is Friday, and then I remembered there was a video with Craig stating the truth, so I made this quickly. 😅 pic.twitter.com/GjNRrQqG3A / Twitter"
Sorry, I struggle with priorities (my ADHD 🙌🏻), but while I was sipping my coffee, I realized that today is Friday, and then I remembered there was a video with Craig stating the truth, so I made this quickly. 😅 pic.twitter.com/GjNRrQqG3A
Ok enough procrastination, I’m going in. Finally made it to the courtroom. The Hough is already roasting Craig and confronting him about the latest forgeries.
Craig replies, as usual, “Achually, that is incorrect.”
Today is going to be fun. 💪
Hough cross-examining Craig on the emails released this week: “These emails are forged, aren’t they?”
Craig: “No, if you show me the header, I will show you that these emails were spoofed and sent to Ontier.”
Hough: “Dr. Wright, these emails were presented by Shoosmiths.”
Hough: “Let’s try the difficult challenge of answering the question, just other than those two differences (the word shared and the word X), can you point to any differences in the face appearance of these two emails?”
Craig: “Um, Again, the questions irrelevant, what I’m answering is the fact that I can’t pick up difference by looking at them, that is why people spoof emails that is why Adam Back…”
Hough: “Dr. Wright, pause there.”
Craig: “Mimecast is fairly open for [missed but he’s implying he’s been hacked again].”
Hough: “Dr. Wright you have suggested in the last 10 or 15 minutes that, this email which was identical to a real email from the 2nd of December 2019 was spoofed on Sunday, the 18th of February 2024 to Ontier.”
Craig: “That’s correct. Yes.”
Hough: “And who do you say did this? And why?”
Craig: “Oh, why is easy? Because I mentioned it in this court case My Lord, and spoofing, isn’t difficult.”
Hough: “You’re now saying somebody would have to get the content of a REAL email from your systems, and spoof an email with that content, backdated to the 2nd of December, 2019, AND spoof that sending it to Mr. Cohen at Ontier on Sunday, the 18th of February.”

Craig: “No, the date field is enterable so I can if I open up a telnet session report, on an email [technobabbling nonsense], there are at least 100 people that I can name that have copies of my email.”
Hough: “So, let me get the straight: somebody’s managed to get hold of your real email, in a native format and spoof an email to Ontier, that’s your position?!”
Craig: “Achually my email is sort of shared now, it’s not funny. Um, I noticed on the weekend, that people have been sending files. Um, to some of the COPA supporters.”

Hough: “That this entire explanation is nonsense, isn’t it? Not only does not account for the encoded image timestamp, which tells its own story, but it would require somebody to get hold of your real email and spoof it by an elaborate process which you have now told the court about for the first time, right?”
Craig: “No, it’s not elaborate. There are tools online for spoofing email that allow you to actually do this by clicking on a website. I know at least 100 of those.”
Craig (continues the nonsense): “This is one of the simplest simple attacks. Someone who’s been a hacker for less than five minutes can do this. Now, I’ve also noted and in the Tulip Trading case, My Lord, I was hacked. In that case, I had a hack of all of my Google email all of my Google files, which were taken. Drives etc, containing emails.”
Hough: ”The reality is that you hadn’t decided what version to give to the court, which email to attack when you wrote your 15th witness statement, isn’t it?”
Craig: “Achually, AlixPartners are engaged by Ontier to do something, so it’s their fault. Or maybe it’s Google’s fault. Oh achually it was @agerhanssen (have you missed me? 🙃)
Hough: “None of this material has been provided on your behalf to support your version of events Dr. Wright. You created a new email from reply to Mr. Cohen’s email of the 2nd of December 2019, didn’t you and backdated your clock to the 2nd of December 2019, didn’t you?
Craig: “Well, that’s actually ridiculous.”
Hough: “Let me explain what you have done. You altered the timestamp in the header to the 2nd of December. Then your wife sent it to Shoosmiths to back up your dishonest story.”
Craig: “Uh, again, if you send an email from Outlook like you’re saying Outlook, doesn’t send that into the Google mail folder [more nonsense].”
Hough: “Dr. Wright, that’s all disputed. Let me give let me ask you one final question, I’m giving you one last chance to confess to this forgery because it may be relevant to relief. You forged this document, didn’t you?
Craig: “No, as I noted.. my Lord. Um, very simple, this is why we need distributed systems. If you do it locally you can cheat. On Google… Google records... To attack Google you would have to change their internal servers. There are I believe 18 of them. You would have to attack multiple databases. We’re talking a state level attack. My Lord. It has happened before, that was the Iranian government...”
Mellor ignores him.
Hough (almost felling sorry for him IMO): “No further questions.”
Gunning is up now.

More forgeries displayed on the screen. Craig Orr (Craig’s lawyer), is now briefly cross-examining CSW. His tone is markedly disappointed, at this point he too has lost faith in Failetoshi.
Mellor now questions Craig: “Dr Wright, you mentioned earlier that someone must have spoofed your email and you said that there can be 100 people possibly suspected of that. Can we be any more specific than that?”
Craig: “Unfortunately not... I suspect a number of people who’ve been fired by my organisation that I’ve been associated with, and that have fled the country. (@agerhanssen dat you?) Can I actually pinpoint and definitively say this? No, what I do know is that information has been on certain Reddit and other discord sites. And also @Arthur_van_Pelt for instance has been taking screenshots of certain information.
Craig: “So there are a lot of people who want me to fail and the BTC Ponzi to keep going. So I can’t even say that they’re directly linked to COPA.”
Hough: “Just, just pause. Dr Wright, your position is that the person who did this, sending the spoof email on the morning of Sunday, the 18th of February 2024. Happen to be doing that on exactly the same morning your wife was sending through a real version of the same email just by coincidence?”
Craig: “Unfortunately.”
Hough: “On the same morning as your wife sent through the real version of the same email and that was a complete coincidence?
Craig: “I don’t know if it’s a complete coincidence.”
Mellor: “Who else would know you were doing that?”
Craig: “I haven’t had my house bug swept recently, and that’s not something that hasn’t happened before. Diligence have come through my house twice. They’re a private intelligence company, my Lord, and on both occasions I’ve had bugs in my house. Um, we’ve had multiple break-ins, because… (more bullshit).”
Mellor: “Lunch break”

Lunch break and coffee with @BitMEXResearch and @WhatTheFinance9.
We’ll be back in court in 10 minutes.
Patrick Madden on the stand, by CryptoDevil

We are back after that mad morning with CSW, now on to Mr Madden being recalled as a result of having to do an additional report to his earlier ones to deal with these forged emails.
Madden: *swears in*
H: *brings up this 5th report and asks is there a correction needed*
M: “Yes in my haste to get this report completed I used the term ‘soft fail’ when it should have just been ‘none needed’.”
H: “A few matters, do you recognise this as the document you call the ‘Ramona Version’ as the one from Ms Watts to Shoosmiths of Feb 2024”
M: “Yes”
H: “And on the following page where you discuss the header as having anomolous data for 2019 in it. That I put to CSW that the header format was not consistent with one from 2019 and he answered that it was not the full email sent and I pointed out that the header size was not consistent with a 2019 email and he said [CSW’s waffle about account migration being the reason], what do you say to that explanation he gave?”
M: “That I do not think this would result from an account migration”
H: “This the 18th February 2024 received version which is with the face data showing it as dated 22nd December 2019, which Ontier say they did not receive until February 2024. What CSW said about this ‘it shows spoofing more sophisticated than would generally happen, some of the authorisation values et cetera don’t generally happen’. His reason for why he said it was spoofed, he said [CSW’s reasons for why it wouldn’t have been Ontier] and he spoke of it going to a spam box and [spoke of DKIM and ARC signed message]. What do you say to his explanation that this email was a spoof, not sent from his email?”
M: “There are no indications it has been spoofed, no DKIM or SPF showing it as having been spoofed. It is possible that mimecase could be used for such but that this email does not show signs of that”
H:”And what do you say to CSW blaming it on Google server’s handling?”
M: “No that’s not relevant and that the header is consistent with a valid email”
H: “What do these pages tell us about the SPF config information in relation to jcjbr dot org and tuliptrading dot net?”
M:”This shows DNS history for them and the rcjbr historial TXT data shows that between 2017 and early February 2024 there was no TXT record and that as at 28th February 2024 it shows it being populated with one. Page 4 is MXToolbox record for rcjbr shows the current record contains an SPF check for google dot com rcjbr dot org”
H: “What do these reports tell you?”
M:”They tell me that as of the 24th February 2024 there was no SPF config set up and that between then and the 28th February 2024 it was added. For TulipTrading as of this morning it is showing there is no SPF, no TXT record is shown. In this report is shows that as of this morning one was added to Tulip Trading. This TXT record is showing that the record did not contain SPF for 21st of March 2021 to 22nd February of 2024.”
H: “And what does all this tell you about the SPF config in relation to that site”
M: “That the SPF record was added to after 22nd Feb 2024”
H: “Those were all my questions”
 Craig Orr KC
Craig Orr KC
Orr KC for Wright takes over.
O: “You are familiar with the term email spoofing?”
M: “Yes”
O: “This is an extract from the Cloudflare website. If we look at the first para it says [describes what CF say is what email spoofing is and how it works] it says attackers use scripts to manipulate the from and reply-to address, do you see that?”
M: “Yes”
O: “If you read on from there where it says ‘email spoofing is relatively easy’ my question simply is that an accurate summary of how email spoofing works”
M: “It CAN be easy, it depends on where you are inserting your spoofed email. If you have an insecure system it can be taken advantage of”
O: “So an email spoofer can make an email message seem to come from a different sent. It exploits a vulnerability in SMTP”
M: “Not all SMTP is vulnerable but it can be”
O: “It is relatively easy to do”
M: “If you have a badly configured email server, yes”
O: “So with SPF that allows a domain to broadcast a list of the server authorised to send email from that domain”
M: “It isn’t a broadcast they retain the valid IP’s they approve, the recipient would check against that list”
O: “DKIM allows email to be signed with cryptographic key and the receiver checks that sig against the pubkey. DMARC are policies that specify what a mail serve should do against these sec settings”
M: “Yes”
O: “In addition to spoofing the sender it is also possible to manipulate the SENT date and time of the header?”
M: “Yes it is”
O: “Your report you say this kind of spoofing can be done by manipulating the computer clock of the sender’s computer”
M: “I wouldn’t call this spoofing, that is more about identity, this is just about backdating a message”
O: “Yes but it is about fabricating an email to make it look like something it isn’t. Now while backdating the computer clock can achieve that, it is also possible to use tools to do so. Your first report, you say ‘spoofing in this context refers to sending an email as though it comes from the sender it is purporting to and that it is possible to spoof emails using online tools, such as mkai dot cz which can be visited in a browser window and an email filled out and sent without validation or payment.’”
M: “Yes”
O: “This extract from the Microsoft Learn website discusses Powershell and this example has a box showing an extract from an email header”
M: “Yes it is the instructions you would use in powershell to generate an email message”
O: [reads the MS page about powershell] this allows someone to fill out the necessary elements of an email to send”
M: “Yes this is doing what your email platform would normally do”
O: “Here on this piece about Netcat it discusses spoofing an email, fooling an email client, like Outlook”
M: “Yes”
O: *reads through the article describing the commands to generate a date string that resembles a specific date*
O: “It is right that using this tool one can specify not just from and to but also the date field”
M: “Yes”
O: “What we see on this doc is the header of an email that you sent to yourself as a test. This is the experiment you describe in your 6th report and you explain that you sent this using Outlook 16.0 via Gmail with a backdated computer clock”
M: “Yes”
O: “There the line begins ‘authentication-results’ which shows the SPF check and DKIM check has been passed. It notes the DMARC policy as pass action=none”
M: “I haven’t looked at all the detail of it as I generated it so knew its history”
O: “What are you doubting?”
M: “I’m not doubting anything, I sent it so I didn’t need to review those elements”
O: “What might you need to investigate with this?”
M: “What I wanted to do was to form a benchmark of what a typical Outlook header would look like with the clock backdated, so sent one”
M: “When comparing the Ramona version with the 18th February 2024 version a lot of common characteristics clearly showed them as being related but there also being other disparities between them, like the header ID, I wanted to figure out what activities would replicate the same”
O: “You said ‘to be honest I didn’t expect it to successfully send’, why?”
M: “Quite a few providers have well set up systems and would not allow and old message to be sent. It wouldn’t get the smtp and transmission heads applied to it. The transmission header would not be populated until it got a transmission through a mail server. If you have not set up you server to prevent this sort of old email transmission, it would go through and it would appear Google did not go through]”
O: “So by the providers of ‘well set up systems’ you would say Google, wouldn’t you”
M: “Yes, I would. I didn’t expect it would go through. I didn’t use the webmail interface though, which would have rejected it”

O: “The 18th of February 2024 received version header is on page 10 and you agree there is no SPF, DKIM or DMARC in it”
M: “I agree”
O: “On the same email you say ‘in the 18th of February 2024 the email is sent from craig at tulip trading dot com”
M: “Sorry that should have been an errata”
O: “You meant tulip trading dot net”
M: “Yes”
O: “That email address appears in the From field of the email address, you cannot say whether that has not been spoofed. It could have been spoofed by a 3rd party couldn’t it”
M: “It does not show any indication of having been spoofed. Having SMTP auth had been a steadfast requirement for some time”
O: “No I am saying this email COULD have been spoofed by a third party”
M: “No I disagree”
O: “You would expect a genuine email from tulip trading to have passed authorisation checks if they were in place”
M: “If the recipient had done these checks yes”
O: “You were shown DNS records and you would accept they are only as accurate as the data collected by the recipient services”
M: “Yes, I have said that many times throughout”
O: “What this record shows is as at 26th May 2017 there was no SPF check set up”
M: “Yes”
O: “It also shows that as of the 24th February it was set up, what you cannot say is when it was set up between this period. This is what you said when it related to the Abacus emails”
M: “Correct, yes”
O: “Now we see here that the December 2019 date is highlighted in green, which clearly is inconsistent with the 18th of February 2024 date we see highlighted in yellow and that we see it is consistent with the email having been sent on the 18th of February. That is is consistent with the sender backdating their computer clock. But they could also have used a tool to do so”
M: “Yes but it depends what you want to do”
O: “But It could be done with appropriate tools”
M: “With significant effort yes”
*O and M repeat same*
O: “Now for the Ramona email that was sent from craig at Tulip Trading dot net and your view is that it was sent on 18th February 2024 from a computer with a backdated clock”
M: “Yes”
O: “Well, we will dispute that but first let’s go to your report. Where you describe your test”
O: “You say that this test was carried out using a local version of Outlook. It is right that an email sent in the way that you described would not appear in the sent folder of the Google webmail interface”
M: “Yes, it would”
O: “It would NOT appear”
M: “It does”
O: “Here it doesn’t actually identify the email sender as anything other than ‘craig wright’ you have not analysed that particular email in your report”
M: “I wrote the report before that was provided”
O: “You were asked by Mr Hough about the emtmpsa timestamp and you told him that you did not think…”
M: “That migration would account for the anomolous information”
O: “Yes, this is not something you have tested for”
M: “No”
O: “These were all my questions, My Lord”
Hough KC returns for a few clarifications.
H: “You recall the questions about the 18th of February 2024 received email and that Mr Orr asked you some questions suggesting the possibility that email had been created by spoofing and that one of the things the spoofer would have to do is authenticate with google. What effect would 2fa have on that process?”
M: “If you are sending from an account with 2fa Google it will keep it pre-authed for some time. Your apps can stay authenticated for some time”
H: “All my questions, My Lord. That My Lord concludes the evidence”
M: “Finally. So I look forward to receiving your closing remarks by next Friday 4pm.”
Grabiner: “will there be a limit on the evidence we can provide?”
M: “I’m not going to place any restriction on the evidence. So far both sides have been reasonable, I mean all three sides have been!”
*laughter*
The curtain drops and the house lights go up! The audience slow claps for another grand show of the Theatre of the Absurd! 🎭
 WizSec Bitcoin Research with the TL;DR of the day.
WizSec Bitcoin Research with the TL;DR of the day.
Patrick Madden on the stand, by Robin Nakamoto
Hough is questioning Madden about Craig’s claim that the Ontier email was spoofed.
Hough: “Now, what do you say to Dr Wright’s account and explanation saying that this Email was a spoof and not sent from his email address?”
Madden: “There are no indicators that it has been spoofed. There is no SPF Check records there’s no dmarc in this header.”
Hough: “May ask you to be handed a short tip of papers, which we, I, handed to His Lordship at the start. Thank you. Mr. Madden, could you explain what we see on each of these pages. And what they tell us if anything about the SPF configuration information In relation to the two domains https://rjbr.org and https://Tuliptrading.net."
Madden: (explaining snapshot check-ins on what txt records are hosted in the txt domain record bla bla IT security guys stuff)
Hough: “Taking those records together. What if anything do they tell you?”
Madden: “About the SPF configuration information and when that was added. It was added sometime after the 24th of February 2024.”
Craig’s Orr KC (CO) now cross examining Madden.

Basically, the whole trial now isn’t even about who Satoshi is anymore, but it’s all about spoofed emails and trying not to let the IT security guys end up in jail.
cc: @Snowden
Madden has finally concluded his “Internet for Dummies” lesson, allowing CO to return to his nap. It’s now Hough’s turn to cross examine.
Done, I need to snap a photo with the Hough.
I got distracted talking to someone outside the courtroom and missed the Hough.
No selfie. 😫

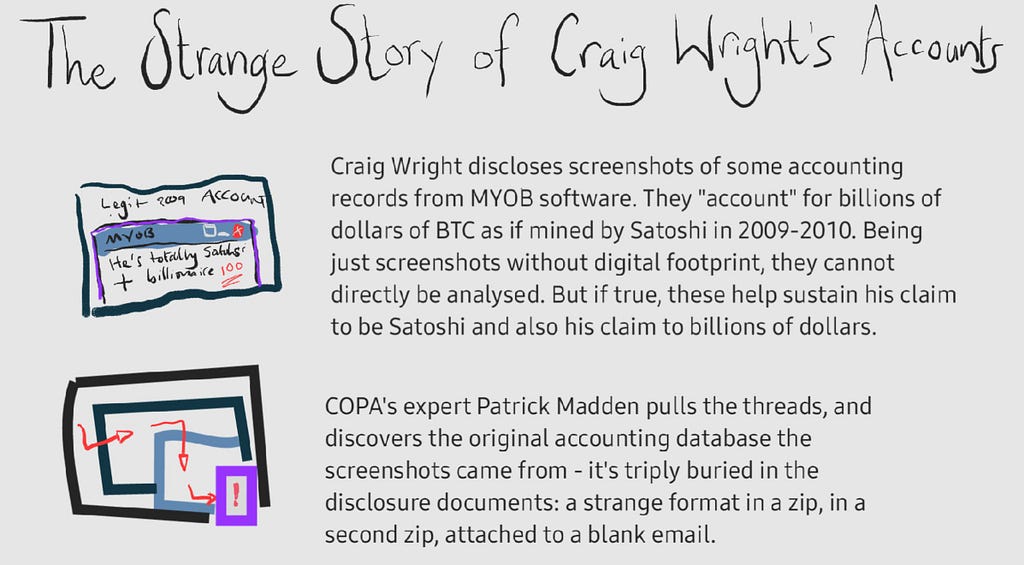
The Strange Story of Craig Wright’s accounts
On March 3, 2024 an anonymous PDF file with a cartoon about this fraudulent email case popped up on Reddit, happily endorsed to a certain extent by Reddit user ‘nullc’ (who is actually one of the parties in the COPA v Wright Joint Trial, (ex-)Bitcoin developer Greg Maxwell).
“I think this is pretty good! Though it fails to capture the point that this MYOB data is only data that support's Wright's lawsuits: No payroll, no ordinary business expenses, just a handful of transactions to explain exactly what he needs and nothing else.”
The cartoon is just too good to not consider including in this article.

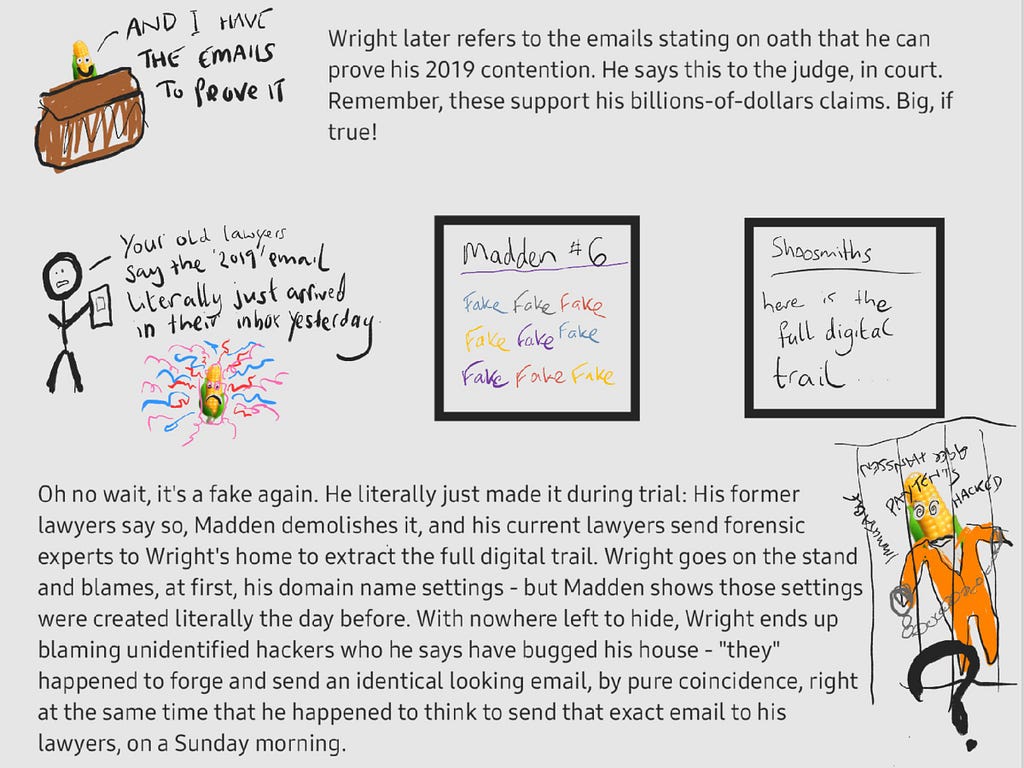
Then the extensive explanation of Reddit user ‘StealthyExcellent’ as a response to the cartoon cannot be missed either. StealthyExcellent goes to great lengths to make sense of Craig Wright’s convoluted story about the forged and/or spoofed emails.
“Good one. Do we know who made this?
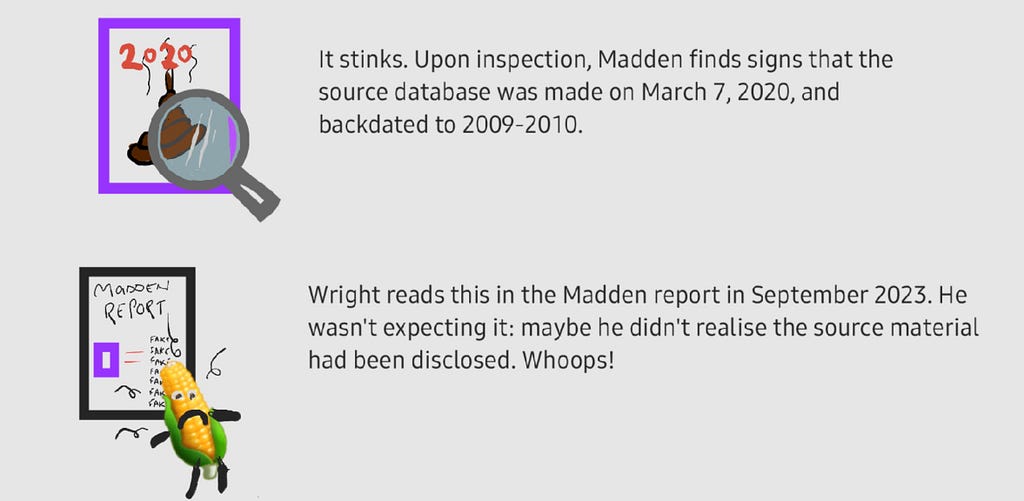
The funny thing is, even if Madden never found the native MYOB file buried within the zips of the Shadders email, Judge Mellor was surely never going to rely on mere screenshots of accounting records. Especially not when there are so many findings of manipulation in practically all of Craig’s submissions, and with so many doubts about Craig’s overall honesty.
So even if we had nothing else to go on, it still wouldn’t be very compelling evidence of Craig’s Satoshi claim, as anybody could easily fake similar-looking screenshots. But there is very strong evidence that they were indeed faked. Ontier confirmed in writing they were first provided MYOB login details on 9 March 2020, and they took the screenshots on 9–10 March 2020. That’s only days after Craig provably made the entries in the MYOB database on 6–7 March 2020, according to the audit log.
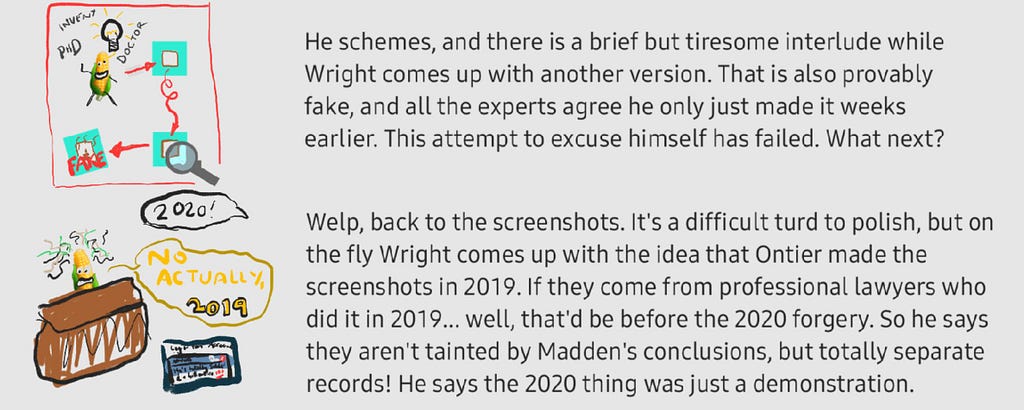
Craig even admits to doing the latter, but he says that was for a ‘demonstration’, much like with his Overleaf metadata explanation. He insists the screenshots themselves weren’t of those ‘demonstrative database’ records, but supposedly of the ‘real database’ that he didn’t disclose. He says they couldn’t have been screenshots of the demonstrative database, in fact, because Ontier got the login details in 2019.
Even if Craig manages to establish the screenshots were from 2019, in a satisfactory way, they could just have easily have been faked in 2019 instead of 2020 then. The judge would still not put much weight on them. If that were the case, we just wouldn’t have positive evidence of Craig faking them in 2019, but they could easily have still been.
Craig at this point is only concerned with dodging the accusation of forgery. Winning the trial with this evidence is not what’s at stake. Craig doubles and quadruples down by making a new provably fake MYOB database in 2023 PLUS a new provably fake Ontier email in 2024. The email is supposedly corroborating that Ontier got the login details on 2 December 2019, just like Craig said, and so Ontier was either mistaken or lying when they said otherwise. What can you even say?
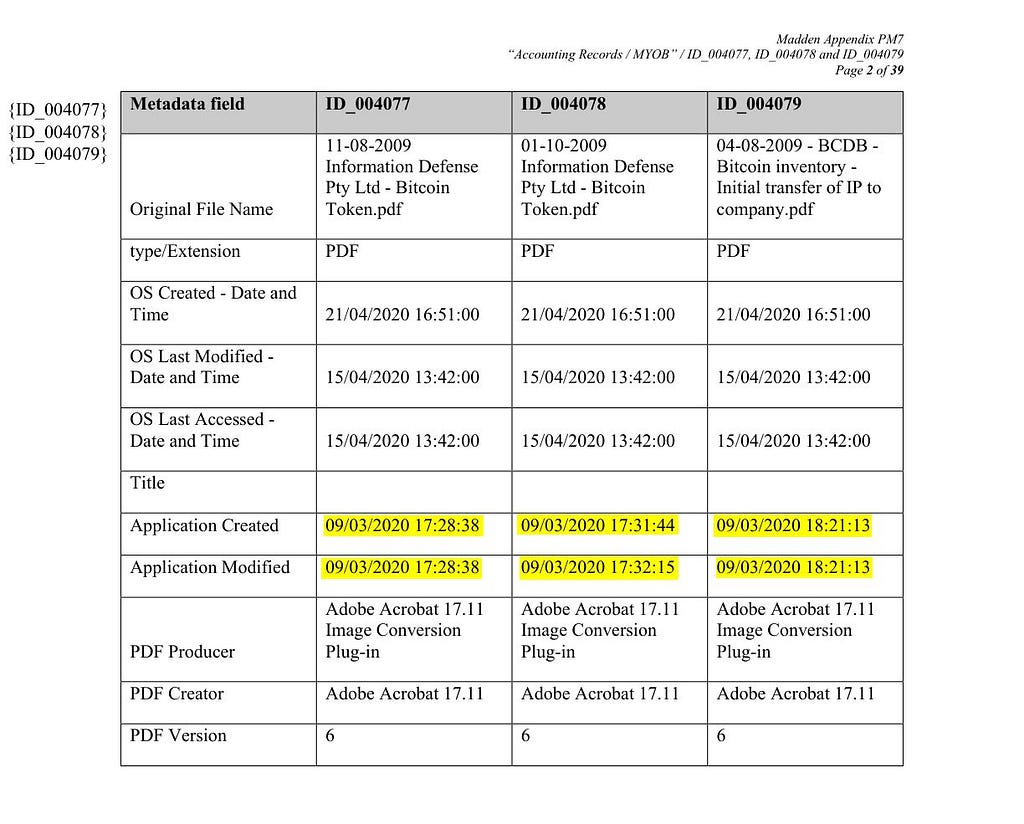
Remember, all of this shit isn’t even for establishing winning evidence of Craig’s. It’s just whether we can prove he faked it or not (to a reasonable standard). And of course we can. The screenshots — which, keep in mind, are Craig’s nominated reliance documents, not just from a disclosure dump — literally have metadata that say they were created on 9 March 2020 (found in PM7 paragraph 3):
Okay. What’s more, the screenshots Craig relies upon were also immediately preceded by other screenshots in the same disclosure set. Those are full-screen screenshots also showing the MYOB database. In those, we can clearly see the Windows system clock of whoever was taking the screenshots. Those show the Windows system date as 9 March 2020 (found in PM42 paragraph 13):
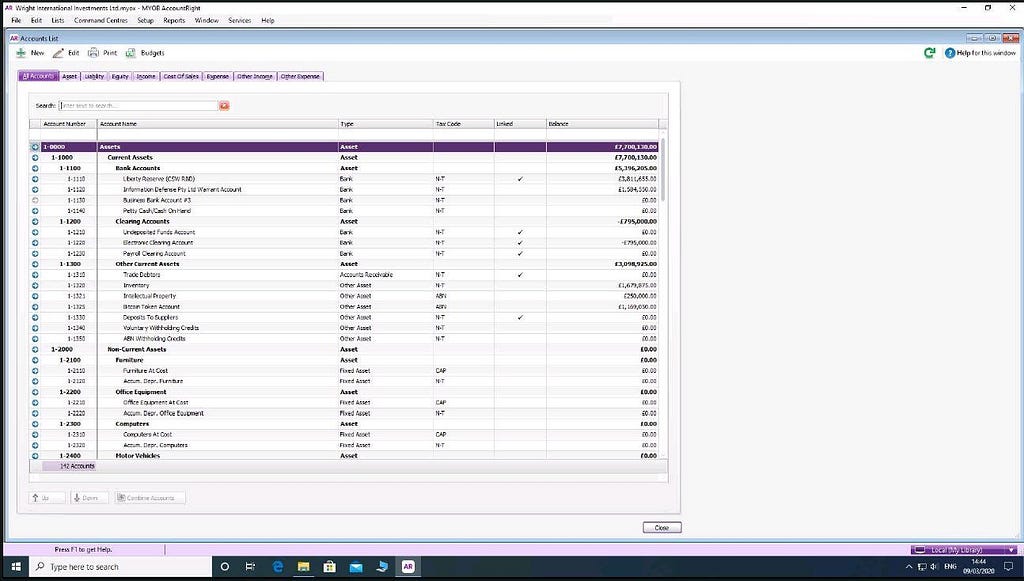
The above screenshot is from ID_004076. Compare that with the ID numbers on the metadata table I linked to above, which are Craig’s three reliance documents (ID_004077, ID_004078, and ID_004079). And yet again, the metadata of ID_004076 also says it was created within hours of Craig’s three reliance screenshots (14:49:14 on 9 March 2020). So they were all very clearly taken at the same time, on 9 March 2020, in the same series of screenshots.
Put that together. The idea that these series of screenshots weren’t actually created on 9 March 2020 like Ontier confirmed, but sometime closer to December 2019 like Craig insists, is absurd just from this alone. It should be case closed.
So this is incredibly bad for Craig, and this alone could justify perjury charges. So Craig desperately forges a Hail Mary email in the middle of the trial supposedly showing he did actually send Ontier login details on 2 December 2019 like he insisted. But Ontier quickly confirmed it wasn’t on their systems in 2019. A very similar email was, but which never mentioned MYOB. That was just Craig sending them a document about BlackNet. The forged email was on their systems though, but it was first received on their systems on 18 February 2024, but which on its face says 2 December 2019. So Craig must have forged it and sent it to them on the 18th, and hoped they would find it and back up his story, which is an incredibly desperate move by an incredibly desperate man.
BSVers think Craig did really well on the last day when answering questions about this. It’s honestly sad that they’re so deluded. Craig is on the verge of being sent to prison, but they’re so deep in their delusions that they think he’s on the verge of winning it all. There’s some truth that Craig does ‘well’ on the stand (in the sense that he is a skilled liar), but that also exposes the lie that Craig needed special considerations due to Asperger’s. Remember that Craig was literally asking for cross examination questions to be put to him in advance, and in written form, etc. Can you imagine? Seeing his performance in the witness box over many days, how can anybody think he needed that? I think Craig arguably looked more comfortable in the witness box than any other witnesses in the entire trial. Literally.
Craig is very good at projecting false confidence and preparing ‘answers’ so that it appears he’s never stumped (except when it comes to telling us what the ‘unsigned’ keyword means). But the judge isn’t going to care about that. He’s going to care about the substance of what Craig is saying, not the fact that he is saying technical things confidently. Craig can never back anything up with corroborating evidence (that isn’t itself fake, at least). He gives excuses very skillfully that could theoretically be the case sometimes, but which are highly, highly unlikely (so this is literally the Dumb and Dumber, “So you’re telling me there’s a chance?” meme). Other excuses aren’t even possible at all, but again he delivers them confidently, and it makes it sound like he knows what he’s talking about.
If Craig says his house was probably bugged to explain why an adversary coincidentally sent a spoofed email to Ontier (spoofed to look like it was coming from Ramona) on 18 February 2024, at the exact same time Ramona sent a non-spoofed copy of the same email to Shoosmiths, the judge has no corroborating evidence of bugs, and it just sounds fantastical and highly unlikely. It doesn’t actually matter that Craig delivers that story very confidently. When Craig says he did some private tests, the judge has no corroborating evidence of that either. He needs to instruct his expert to do those tests, not do them at home and just tell us what his results supposedly were.
We must also remember when Craig said he personally tested every single version of Pandoc, and none of them output the string that was found in Craig’s document (which would date it to later than 2007). Craig said Ager-Hannsen put that string in there manually, during a hack of his laptop whilst the drive was plugged in briefly, in order to make it look like it was converted using Pandoc. Again, this is Craig just saying fantastical things and referencing results of private tests conducted by him, not his expert, so it doesn’t even matter. But John Macfarlane, creator of Pandoc, then produced his second report easily showing that every version since 2.7.2 (which is from 2019) does in fact output that string. He produced a script that automatically downloads every version, and gives easy instructions for how to check for the presence of the string. After that, Craig’s team decided not to even cross examine John Macfarlane. So much for Craig’s private ‘testing’ that the judge was never going to rely upon anyway.
BSVers think it makes more sense that the new Ontier email is real and Craig’s house was bugged like this is some kind of goofy spy novel, and some spy sent a spoofed email to Ontier hoping it would get found by Ontier and disclosed to Bird & Bird to make Craig look like he was faking it, even though on its face it supports Craig’s position. They think the original genuine email about BlackNet was really Craig replying to the same email twice, but with two completely different responses to the question ‘What is this?’ by Simon Cohen. Come on. Remember, the screenshots are clearly from 9 March 2020. So Occam’s Razor suggests that this is just a newly forged email. Think of all of the extra fantastical things we now must believe in continue to trust Craig’s story that the screenshots aren’t of the fake 6–7 March 2020 records, but are actually from 2019.
Also, Craig’s spy adversary would have to be banking on Shoosmiths emailing Ontier to check with them, and Ontier finding the ‘spoofed version’ but not the original genuine version from 2019, because it was supposedly lost to their spam folder. The spy adversary wouldn’t have known they would fail to find it unless they hacked Ontier too, or they are internal to Ontier. What’s more, if it was lost to the spam folder, this would also mean they wouldn’t have logged into MYOB in 2019 to take the screenshots either, so it doesn’t even help to establish the original point. Then the spy adversary would have to be banking on Shoosmiths disclosing the ‘spoofed version’ to Bird & Bird, instead of it just being kept hidden by Shoosmiths, which was always possible (much like the majority of the Overleaf metadata was).
Let’s also not ignore that Craig changed his DNS records last week specifically to make the SPF test fail, so he can better argue it was spoofed (because it’d be hard to argue it was spoofed if the SPF test passes). I hope the significance of Craig changing his DNS records that week will not be lost on the judge. It looks like it was covered quite a bit, so I don’t think it will be.
You have to be truly delusional to think Craig won on Friday, and that this trial is now in the bag for him.”
Amen to that, StealthyExcellent.
Edit March 6, 2024 Madden’s 6th forensic report
On February 28, 2024 Madden’s report about the ONTIER email forgeries was released. Almost a week later it could be found in COPA’s DropBox.
A snippet from Madden’s findings.
“SUMMARY OF CONCLUSIONS ON EMAILS
35. Considering these findings, in my opinion:
a. The Ontier Version is an authentic email which dates to 2 December 2019, and contains consistent timestamps on its face, on the Transmission header, and encoded in the image attachment properties.
b. The 18 Feb 2024 Received Version was authentically sent on 18 February 2024 and received by Ontier on 18 February 2024. However, it was authored with a computer with the local clock backdated to 2 December 2019. The date on the face is not authentic and has been manipulated by backdating the clock; the dates on the servers that transmitted it and encoded in the properties for the image attachment do accurately record that it was created and sent on 18 February 2024.
c. The Ramona Version is not authentic to the purported timestamps. It is a sent item that has been manipulated to change a human-readable timestamp to match the date on its face. Since it is a sent item and does not record any further server hops, there is no transmission information; however the timestamp encoded in the properties for the image attachment indicates that it was created on 18 Feb 2024.
d. I did not find any information that caused me to doubt the authenticity of the Email to Shoosmiths itself, but I did not investigate that email in the same depth as the others based on my instructions and the short time available.
36. Considering the various forensic indications, in my view it is possible to reconstruct the following timeline in relation to these emails:”
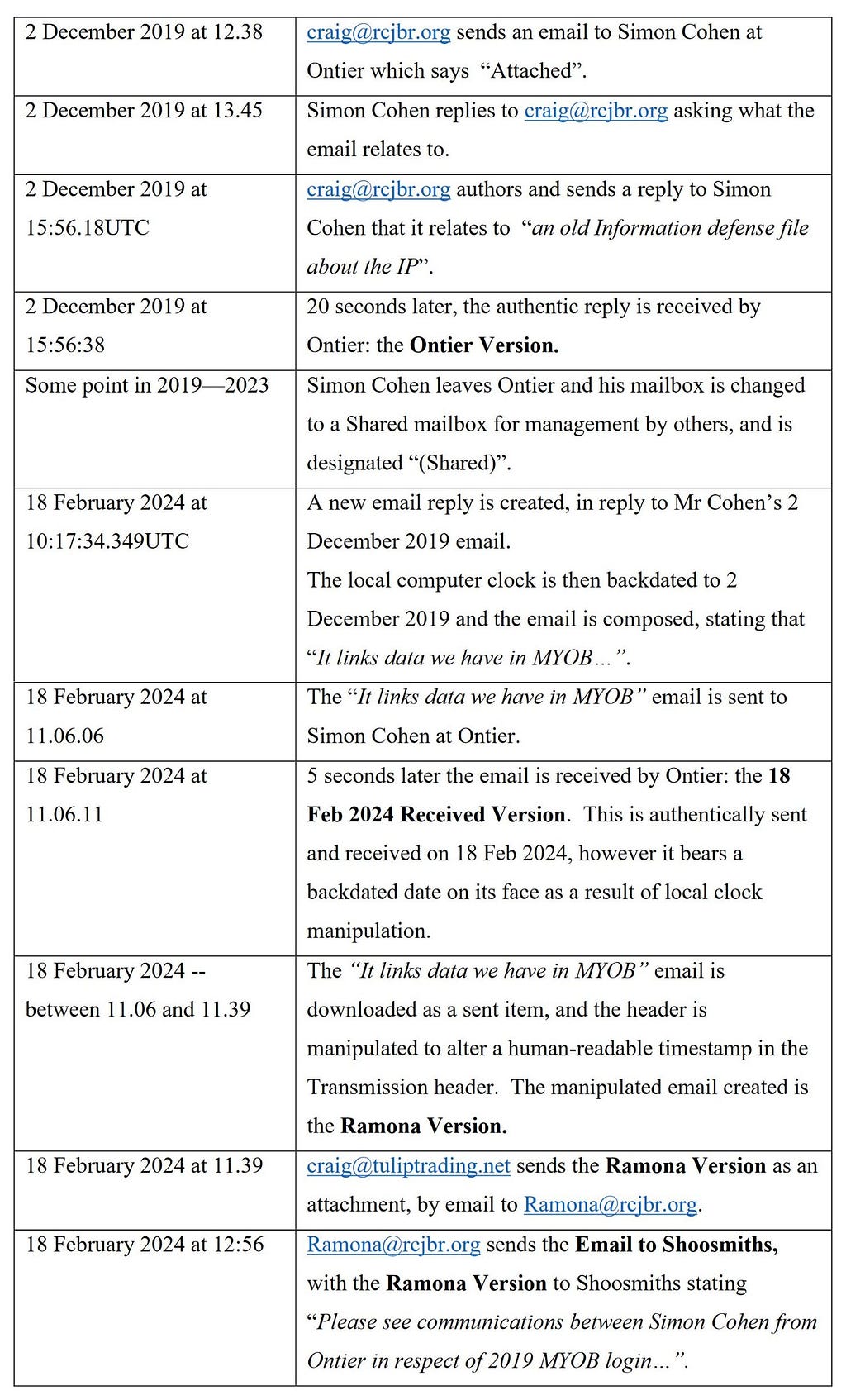
Outro
So far for the transcripts by ‘CryptoDevil’ and ‘Robin Nakamoto’ and the cartoon. This article described my third favorite COPA v Wright Joint Trial moment, about an email forgery that Craig Wright created on February 18, 2024 which is contributing to a series of ‘fraud upon the court’ events that Craig has been building in 2023 and 2024.
It is my more than educated guess that Justice Mellor is not going to have a lot of mercy with Craig Wright while ruling about these blatant attempts to pervert the course of justice.
The previous two favorite moments were described in “The IT Security Guy v A Random Lawyer: Who Is Satoshi Again?” (aka Craig Wright can’t code) and in “How Adam Back And Martti Malmi Killed Craig Wright’s Hope Of Ever Winning The COPA Case” (aka Craig Wright has no connection whatsoever with Bitcoin history).
Now what were your favorite moments, dear reader?
Satoshi’s timezone worry? Or the unsigned integer fail?
Or was it perhaps Justice Mellor’s legendary sigh “yeah” to Craig’s admission of notorious backdating?
That’s all folks, thanks for reading again!






